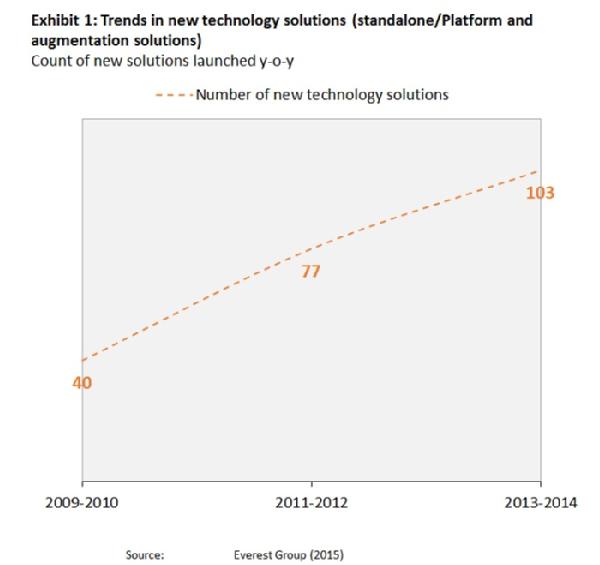
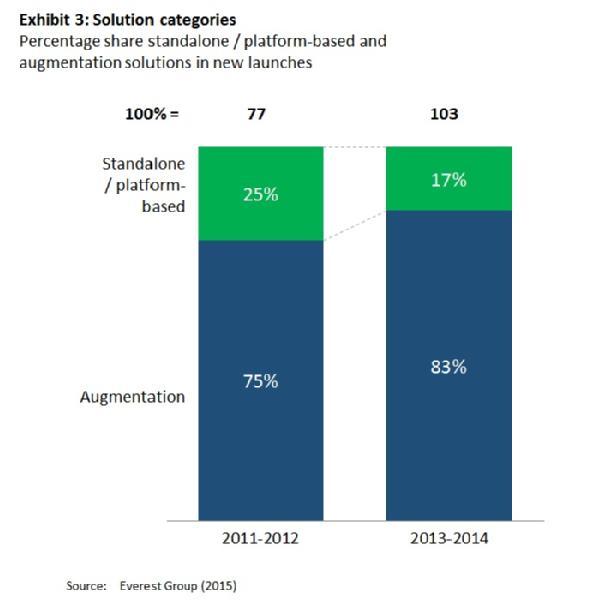
Merger and acquisition activity is at record levels, requiring selling companies to renegotiate outsourcing arrangements for their divested entities.
Merger and acquisition deal announcements hit an all-time high of in 2015, from Anthem and Cigna to EMC and Dell. And experts expect robust M&A activity this year. But just as major mergers lead to major integration efforts for IT, they also spell significant work around outsourcing arrangements. In fact, the selling company is typically responsible for negotiating new sourcing services agreements before a divestiture is complete.
Not only is the seller often obligated contractually to ensure that the divested entity can operate once it is removed from the seller’s IT infrastructure, “there is always a risk that the sale may be delayed or cancelled, and unless the seller negotiates the right to terminate the new agreement if the sale fails to occur or exercises its right to terminate for convenience, it is now contractually bound to receive those [IT] services,” says Derek Schaffner, an attorney in Mayer Brown’s Washington DC office and member of its business and technology sourcing practice. What’s more, if the seller is actively involved in M&A transactions, the company will want to handle the issue of outsourced IT services well in order to maximize future sales prospects, Schaffner says.
However, addressing outsourced IT contracts prior to a merger or acquisition can be tricky. There is often a lack of clarity around both the previous consumption of IT services by the divested entity and the future requirements of the purchasing company. Here are six questions the selling company must consider to do this well.
1. How accurate is your historical IT outsourcing information?
The volumes of IT services used by the divested entity may not have been measured individually, which can be problematic for pricing. For example, it may not be possible to discretely identify invoice volume in a finance and accounting deal. In such cases, the buyer and the IT service provider may ask for a period of time (typically six months) to develop a baseline of IT services volume followed by an adjustment in pricing at a later date.
“The seller should push to include contractual provisions that describe a formulaic method to set the new volume baseline,” says Schaffner. “If the new volume baseline is significantly higher, the new owner may be faced with a large one-time invoice. To the extent that the new volume baseline deviates significantly from the initial assumption in either direction, the provider’s solution may not be appropriately sized and the parties will need to engage in further contract negotiations which may increase the absolute price or the cost per unit price.”
2. Do you understand the buyer’s unique requirements?
“The buyer may have a different risk profile and set of policies that the provider will need to adhere to,” says Schaffner. However, the acquirer does not have any contractual standing to negotiate terms until the new agreement is assigned to them, and the seller is not always aware of the buyer’s specific positions. The service provider may be willing to accommodate changes after assignment, but bargaining power may be reduced at that point.
Schaffner suggests that the seller solicit buyer input upfront on key legal, commercial, and technical terms. “Subject matter experts of the acquirer should have the opportunity to vet the statements of work, service levels, and pricing since operational ownership will transfer to them after the sale of the divested entity,” he says. “Likewise, the acquirer’s legal representatives should be consulted to provide input on items such as liability caps, termination rights, and intellectual property rights.”
3. Will the terms of a cloud-based deal work for the new entity?
Companies are often eager to start up new IT services for an acquired entity as soon as possible, so cloud computing options may seem like the natural choice. But, notes Schaffner, “as with any cloud agreement, there are tradeoffs between the ability to negotiate customized terms vs. the speed to deploy the solution using the provider’s standard terms.” Typically cloud contracts will stipulate terms that may prove problematic for the buyer, such service-level credits as sole and exclusive remedies, limited audit rights, the right to store and process client data anywhere and the provision of minimal disengagement services.
“The economics of a cloud solution dictate that the provider is not able to offer more robust terms that the divested entity enjoyed under a master agreement while it was owned by the seller,” says Schaffner. “Consequently, the divested entity (and buyer) needs to evaluate these reduced terms and decide whether or not the proposed solution will meet its requirements.”
4. Is the provider adequately prepared for the ‘hypercare’ period?
In any outsourcing transition, services should be closely monitored during the first three months after the handoff to make sure work is proceeding as planned. Providers typically offer extra resources during this time (for an additional fee) to help ensure successful implementation. This so-called “hypercare” period is even more important in M&A transactions, says Schaffner, due to the number of new players involved.
5. What happens if the acquisition fails?
Companies should include a clause that says the selling entity can cancel the new outsourcing agreement if the sale does not go through, says Shaffner. However, the provider may look to recover business development expenses. “Some, but not all, providers are open to including such a clause,” he says. “Those that oppose including this type of clause typically argue that the seller will most likely want to find another buyer for the entity and, therefore, would still need to contract for the services. These providers also cite that the seller can terminate the agreement for convenience—with payment of termination charges.”
6. What if we can’t deliver a new outsourcing agreement before divestiture?
All is not necessarily lost. A well-negotiated services contract between the seller and the original provider might have included the right for the divested entity to continue to receive services under that master agreement, says Schaffner.
Source: cio.com – 6 outsourcing questions to ask during an M&A by Stephanie Overby